Review: The Absolute Platform with Persistence Technology
Product Information
Absolute is a long-time player in the endpoint security arena, specializing in endpoint visibility and control.
Regarded as an industry leader in IT asset management for more than two decades, Absolute recently revamped its solution to leverage its patented Persistence technology. The Software-as-a-Service platform is made possible through innovative endpoint technology and go-to-market partnerships with more than 25 original equipment manufacturers (OEMs) and top PC vendors.
Absolute’s patented technology is built into the firmware of more than 500 million endpoints and now extends to third-party applications giving them the power to protect every endpoint, remediate vulnerabilities and maintain compliance in the face of security threats.
Agents and Persistence
One of the things that makes Absolute’s different is that the platform doesn’t require the installation of a new hardware appliance or changes to the organization’s network (e.g. punching holes in the DMZ). The embedded technology detects when the Absolute agent is installed and is activated when it sends its first beacon to the monitoring center.
After the initial activation, the managed device will get a unique identifier and will appear in the cloud-based dashboard.
The previously mentioned firmware-embedded Persistence technology thwarts attempts to disable the software. Should an end user attempt to format the operating system or change the hard drive without the authorization of their IT department, Absolute persists its agent back onto a new OS or hard drive. Absolute’s technology resides in the device’s firmware (non-flashable BIOS location) so that as soon as something goes wrong with the agent, it self-heals and resumes its normal function.
Besides vendor-partners like Dell, HP, Lenovo, Microsoft, and others, Absolute partners with some 25 top tier OEMs. The firmware-embedded Persistence technology is fantastic, but you can also enroll devices without it. The standalone agents can be deployed on Windows, Mac and Android systems, and support is also provided for Chromebooks via a browser extension.
Device visibility
When we talk about endpoint security, visibility is the basic capability that makes everything else possible. All the devices that report back to the central console will show up in the visibility section. As expected, you can dig deeper within the subsets of the collected data and focus on what’s important to your organization.

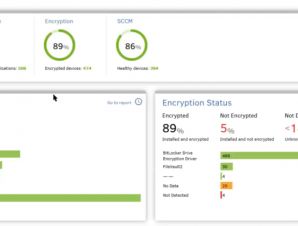
The top dashboard view over your endpoints will show the important aspects that easily slip through the cracks. Anti-malware and encryption status charts identify the exact percentage of the managed devices that have these technologies deployed and what software products are in use. You can easily delve into the detailed report to analyze the findings and see which devices need to get a security upgrade. There are other interesting features of the dashboard, including a list of users that have demonstrated unusual activity, such as multiple logins, access to sensitive data or USB activity – all factors increasing their risk score.
The provided analytics help IT operations and security teams make better decisions and improve the organization’s security posture. Absolute’s cloud-based platform brings the visibility to a new level, as it collects hundreds of attributes from every device. You can spend hours just customizing the device telemetry data and, if that’s not enough, you can extend the view by using custom fields.

In case of a security incident, the data from the endpoints can be used to determine the scope of the risk (types and contents of data, encryption status, etc.), as well as for compliance-related reporting which is increasingly important with GDPR’s 72 hour breach notification requirement. As you can see from just a portion of the data in the screenshot below, every device has a score based on the data types identified on it.

Data protection
Visibility is all good and well, but you’ll need to act on the detected risks. Absolute’s platform can detect different sets of potentially problematic files: those containing credit card numbers, personal health information, personal financial information, social security numbers and those that are encrypted or password-protected, alongside any custom searches an administrator would want to perform. This is useful for protecting intellectual property, or in the case of GDPR, the ability to search for data on EU citizens. The actual content of the file is unknown to the administrator, as that data is not collected and the telemetry is done directly on the endpoint.
Deleting the data at risk is not the only option. Administrators can also freeze the computer and lock the user out of it, beneficial if the device is lost or stolen or an insider threat is suspected.

Application Persistence
I’ve gone through the different mechanism through which Absolute enforces its own Persistence on the managed devices, but the company decided not to stop there. If you can guarantee the resilience of your agent, why not make this functionality available for selected third-party software as well? Absolute did just that with the goal of maintaining and improving an organization’s security posture. Fortifying the managed devices by providing a Persistence capabilities to third-party applications installed on them is a very welcome functionality.
Currently the system works with numerous leading applications, including Microsoft Bitlocker and SCCM, as well as apps from F5, McAfee, Ivanti and others. Even if your specific app is not supported, Absolute can also provide these self-healing capabilities to any application.

Final thoughts
Absolute’s offering provides excellent analytics, quick remediation of potential threats, and offers unrivalled Persistence and self-healing capabilities. I have no doubt that administrators find it extremely helpful and easy to use. Add to this the ease of deployment and you have a perfect endpoint visibility and control solution.
Source: Werzit – Local – Space – Cyber

Recent Comments